Last updated on: December 13, 2024
Azure IDP (Identity Provider) is a cloud-based service that enables authentication and authorization for users to access various applications and resources within the Azure ecosystem. It allows users to authenticate with their existing credentials, such as usernames and passwords and provides a single sign-on experience across multiple applications and services.
It supports various authentication protocols, including Security Assertion Markup Language (SAML), OpenID Connect, and OAuth 2.0, allowing it to integrate with a wide range of applications and services.
Follow below mentioned steps to configure Azure idP with SAML2 in PLEXOS Cloud.
Refer to the region-wise URLs below for each of the environments listed in the Configuration table.
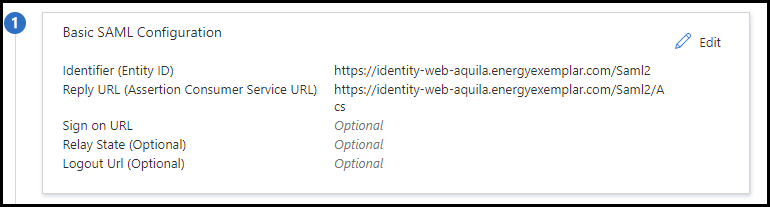
Below table lists out the SAML setup parameters, please refer for setting up the SAML
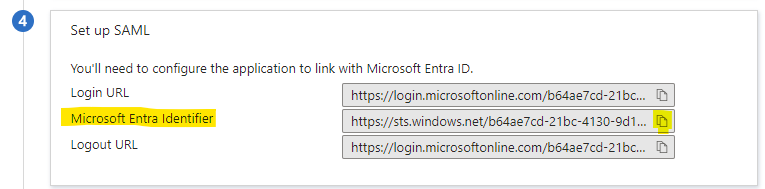
Highlight the url is case sensitive, it should as it is mentioned in Screenshots
|
Key |
Value |
| Identifier (Entity ID) |
|
|
Reply URL (Assertion Consumer Service URL) |
|
|
Sign On URL |
Blank |
|
Relay State (Optional) |
Blank |
| Logout URL (Optional) | Blank |

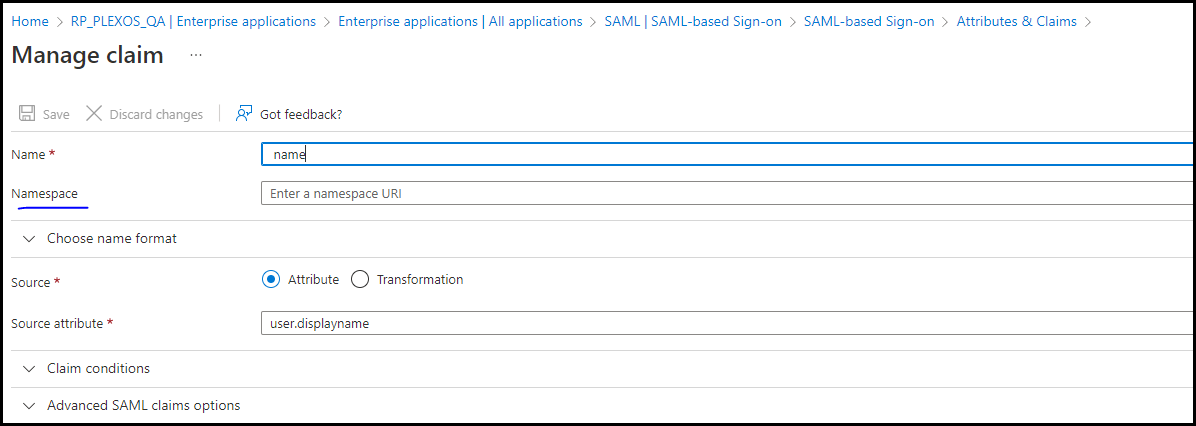
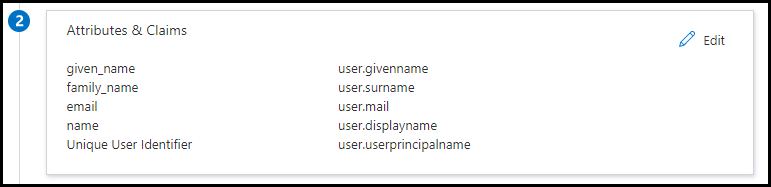
Follow the list below for setting up the Attributes and Claims. Please make sure the value for 'Key' should be in the exact case as mentioned.
| Key | Value |
|---|---|
| given_name | user.givenname |
| family_name | user.surname |
| user.mail | |
| name | user.displayname |
| Unique User Identifier | user.userprincipalname |
 NOTE: Make sure the Namespace field is empty for all the claims except 'Unique User Identifier'
NOTE: Make sure the Namespace field is empty for all the claims except 'Unique User Identifier'
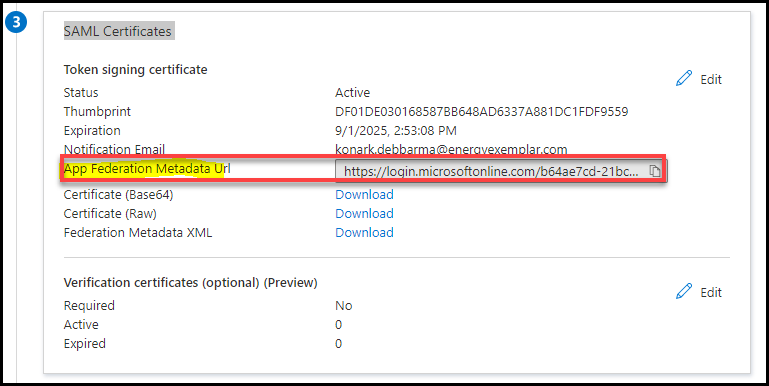
Copy App Federation Metadata URL: This value will be set in EE Cloud Web 'Authority' Field
Copy Azure AD Identifier: This value will be set in EE Cloud Web 'ClientID' Field.